The power of the Tor Browser Bundle allows you to browse the internet anonymously.
Anonymity online is an important issue. Many people use VPNs as a way to stay anonymous. However, many of the VPN services are expensive. Setting up a free one yourself is very difficult.
You can easily browse the internet anonymously without having to configure a VPN or use a paid service. Tor is a client that routes your traffic through a own network and other Tor users. This setup will zigzag and weave your web browsing through many different Tor nodes using encryption.
Picture the service as if someone was following you in real life, and you randomly walked through a maze of stores throughout your city to evade this person. Likewise, in theory, your ISP should not be able to tell what your doing as tor manipulates your network traffic.
Of course, all anonymous services can be used for nefarious means. However, since Tor routes traffic through other Tor users, it is entirely possible that TOR will route some evil activity through your network. As Tor’s network is mainly created through users sharing and rerouting the content for each other, you could be helping other users hide illegal activity. The ethical dilemmas and moral conflicts involved are personal choices for you to decide.
This article is not intended for using Tor to hide illegal manner. Be safe and be smart.
1 TOR has a special package called the Browser Bundle. This is a version of Firefox integrated with TOR magic to streamline the performance. Trying to configure TOR for Chrome or a non “tor-fied” version of Firefox can be difficult and yield very slow connections in some cases. You can download the Tor Browser Bundle here:
https://www.torproject.org/download/download-easy.html.en
2 Once Tor Browser Bundle downloads, we need to extract it. I simply extracted it to my Desktop in this example.
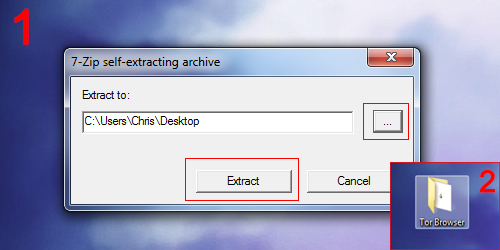
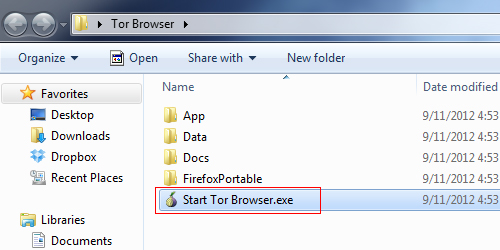
3 Now launch the file called Start Tor Browser.exe in the Tor Browser folder you just extracted.
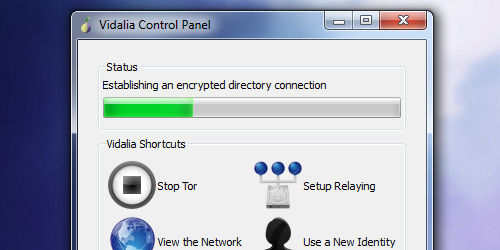
4 A program will pop up called the Vidalia Control Panel. It attempt to connect to the Tor network.
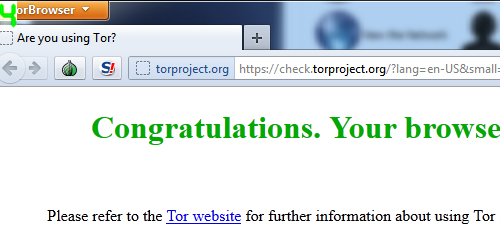
5 TorBrowser will then pop up with a message in green showing that the connection is successful. It will also list your virtual IP address. If you close the TorBrowser, Vidalia will automatically disconnect from the Tor network as well
6 Want to change your IP again? Switch to Vidalia with TorBrowser still open and click Use a New Identity
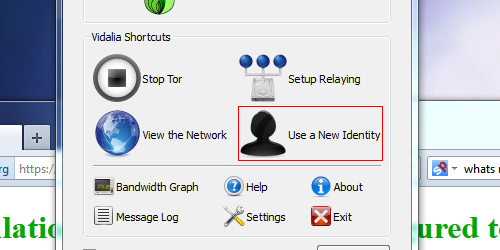
After this you can refresh you page and see that your virtual IP address has been changed. At this point you can proceed with anonymous browsing of the web through the TorBrowser. Remember that by installing additional browser extensions and plugins, you may reduce the effectiveness of your anonymous connection.





